A virtual private network (VPN) is software that is designed to create a virtual encrypted tunnel between you and a remote server that is run by a VPN service. During this process, the external traffic is routed via this tunnel and for this reason; your data will be secure from prying eyes. Additionally, your PC will appear to use the IP address of the VPN server to mask your identity. Alternatively, VPN lets a user connect to the private network via the internet confidentially and securely.
The moment your data is sent to the VPN server, it exits onto the public internet and if the website you are visiting uses HTTPS to obtain a connection, you will still be safe from prying eyes. However, whether it was intercepted, it is impossible to track the data back to you since it tends to come from the VPN server.
For you to understand the significance of a strong VPN, it is good to consider some particular scenarios where a VPN might be useful. For instance, look at the public WIFI network such as at a restaurant or airport. Anyone will rush to connect to this network without having a second thought. This is risky since you don’t know who will be watching the traffic on the network as you browse. Additionally, the WI-FI network you are using might not be legit or it can be run by scammers who are after your data. This means that your important information such as banking data, credit card numbers, passwords that you transmit any time you are online will get into wrong hands if you don’t use a VPN.
In case you connect to the similar public WIFI network with a VPN, you have a guarantee that no second party on that network will have a chance to interrupt your data.
What is a VPN protocol?
VPN protocol is the services and technologies used by VPN providers to make sure that you have a secured and fats connection to their servers and back. It involves a combination of encryption standards and transmission protocols. Normally, VPN providers give their subscribers various VPN protocols such as PTTP, L2TP/IPSec, OpenVPN, IKEv2, SSTP, and SoftEther. Note that VPN protocols come with different architecture and therefore different pros and cons. For this reason, you need to know each of them beforehand.
Best VPN protocols
VPN plays a vital role in protecting your privacy and secure your important data anytime you are using a public internet. However, apart from selecting the best VPN, it is also vital to make sure that you find the best VPN protocol for your requirements. A VPN protocol refers to the means which your VPN will protect the data that is being transferred. There are numerous different protocols that are usually based on the operating system, performance, platform and more.
OpenVPN
This is one of the most recommended VPN protocols and its flexibility and security have made it more popular. It is based on open source technologies such as OpenSSL encryption library and SSL V3/TLSV1 protocols. Since the OpenVPN relies on the open source technologies, it is maintained, updated and inspected by a community of supporters.
The moment traffic goes through an OpenVPN connection; it is not easy to determine whether it is an HTTPS connection or SSL connection. Its capability to hide in plain straight ensures that the protocol is not vulnerable to hacking and making it harder to block. Additionally, it can operate on any port while you use both the UDP and TCP protocol, hence getting around firewalls will not be an issue. Nevertheless, if you want high-speed connection, use the UDP port since it is more efficient.
PPTP
This is also referred to as point to point tunneling protocol that is has been in existence for more than two decades. Despite being old, the protocol is mainly used for internal business VPNs and it’s a popular alternative since it is installed on several platforms and devices. Additionally, setting up this protocol is easy; its effective and no extra software is required. To get a secure connection, you just need a username, password, and address of the server. Point-to-Point Tunneling Protocol works by establishing a tunnel and encapsulating the data packet. It is designed to use a point to point protocol PPP to protect data across a connection. PPTP is a popular VPN protocol that was first used in the time of Window 95.
L2TP/IPsec
Note that the L2TP protocol cannot provide any protection from a traffic that travels through a connection. Due to this, it is mostly combined with an encryption protocol known as IPSec. This is an extension of the PPTP protocol which uses a procedure known as double encapsulation, whereby the first encapsulation creates a PPP connection. The second one comprises IPSec protection. L2TP/IPSec supports AES-256 protection algorithms that are known to be more secure.
Internet protocol security (IPSec)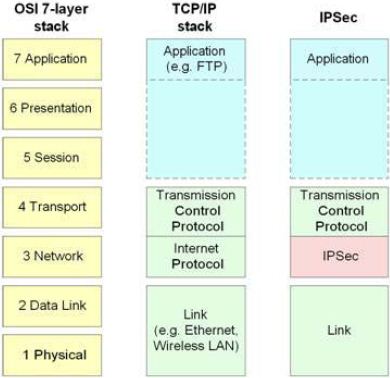
IPSec is utilized in securing internet communication across IP network and they do this by authentication of the session and encrypt each data packet when a connection is taking place. Internal protocol security is designed to run in two modes to encrypt transferring of data between two different networks. The two modes include tunneling mode and transport mode. The work of the transport mode is to protect message in the data packet while the tunneling mode protects the whole data packet. IPSec can be combined with other security protocols to improve the security systems.
Secure sockets layer (SSL) and transport layer security (TLS)
SSL and TLS establish a VPN connection where the web browser serves as the client and user access is limited to the specific application rather than the whole network. This protocol is popularly used by online shopping sites and service providers. Web browsers easily shift to SSL with no action needed from the user because the web browsers are already incorporated with SSL and TSL. Note that all SSL connections contain HTTPS at the beginning of the URL rather than the HTTP.